Enable Disk Encryption for EKS Cluster
Palette allows you to enable encryption on Elastic Block Store (EBS) root volumes for Elastic Kubernetes Service (EKS) cluster worker nodes using AWS Key Management Service (KMS) keys, specifically customer managed keys.
Once disk encryption is enabled, all current and new worker nodes in the cluster will have their root volumes encrypted using the specified KMS key. This includes any disk changes made to the worker node pools using node pool customization.
Enabling disk encryption on an existing cluster will trigger a worker node pool repave, which will replace the existing worker nodes with new nodes that have encrypted root volumes. This may cause temporary downtime for workloads operating on the cluster, so ensure you have planned for this before proceeding.
Prerequisites
-
An AWS account added to Palette. Review Add AWS Account for guidance.
-
The IAM user or role used by Palette has the required policies attached as listed in Required IAM Policies, including the PaletteControllersEKSPolicy policy.
-
The following additional permissions are required for Palette to list and use the KMS key for disk encryption. Add these permissions to the PaletteControllersEKSPolicy policy in your AWS account:
kms:ListKeyskms:ListAliases
Example PaletteControllersEKSPolicy Snippet
...
{
"Condition": {
"ForAnyValue:StringLike": {
"kms:ResourceAliases": "alias/cluster-api-provider-aws-*"
}
},
"Action": [
"kms:CreateGrant",
"kms:DescribeKey",
"kms:ListKeys",
"kms:ListAliases"
],
"Resource": [
"*"
],
"Effect": "Allow"
}
...
-
-
A KMS customer managed key created in the AWS region you intend to deploy EKS clusters using Palette. You will need to provide the key ID when enabling disk encryption in Palette. The KMS key must meet the following requirements:
-
Key type = Symmetric
-
Key usage = Encrypt and decrypt
-
A key policy that gives the AWSServiceRoleForAutoScaling service-linked role permissions to use the KMS key. Refer to the Required AWS KMS key policy for use with encrypted volumes guide for detailed information on the required key policy.
Example Key Policy
{
"Version": "2012-10-17",
"Id": "key-consolepolicy-3",
"Statement": [
{
"Sid": "Allow use of the key",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::111222333444:role/aws-service-role/autoscaling.amazonaws.com/AWSServiceRoleForAutoScaling"
},
"Action": ["kms:Encrypt", "kms:Decrypt", "kms:ReEncrypt*", "kms:GenerateDataKey*", "kms:DescribeKey"],
"Resource": "*"
},
{
"Sid": "Allow attachment of persistent resources",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::111222333444:role/aws-service-role/autoscaling.amazonaws.com/AWSServiceRoleForAutoScaling"
},
"Action": "kms:CreateGrant",
"Resource": "*",
"Condition": {
"Bool": {
"kms:GrantIsForAWSResource": "true"
}
}
}
]
}
-
Enable Disk Encryption
- New Cluster Profile
- Existing Cluster
-
Log in to Palette.
-
In the left main menu, click Profiles.
-
Create a new cluster profile for an AWS EKS cluster. Refer to the Create a Cluster Profile guide for more information.
-
Once you have configured your profile and are viewing the Profile Layers step, click on the Kubernetes layer to edit this pack.
-
Under Pack Details, select Values and use the YAML editor to add the following configuration. Replace
<kms-key-id>with the key ID of your AWS KMS key.cloud:
aws:
encrypted: true
encryptionKey: <kms-key-id>infoThe
cloudsection needs to be added at the top level of the YAML file, not nested under any other section. -
Click Confirm Updates once you have added the configuration.
-
On the Profile Layers step, click Next.
-
Click Finish Configuration.
You can now use this cluster profile to create a new EKS cluster with disk encryption enabled. Wait until the new cluster is fully provisioned before proceeding to validate the disk encryption.
-
Log in to Palette.
-
In the left main menu, click Profiles.
-
Locate and select your EKS cluster profile.
-
Create a new version of your cluster profile. Refer to the Version a Cluster Profile guide for more information.
-
Click on the Kubernetes layer to edit the pack.
-
Under Pack Details, select Values and use the YAML editor to add the following configuration. Replace
<kms-key-id>with the key ID of your AWS KMS key.cloud:
aws:
encrypted: true
encryptionKey: <kms-key-id>infoThe
cloudsection needs to be added at the top level of the YAML file, not nested under any other section. -
Click Confirm Updates once you have added the configuration.
-
On the Cluster Profile page, click Save Changes.
-
In the left main menu, click Clusters.
-
Locate and select the EKS cluster you want to enable disk encryption on.
-
Click on the Profile tab.
-
Click the version drop-down menu for the infrastructure layers and select the new version of the cluster profile you just created, then click Review & Save.
-
In the pop-up window, click Review changes in Editor.
-
In the configuration diff window, review the configuration changes, then click Update.
cautionOnce you click Update, a worker node pool repave is triggered, which will cause the worker nodes to be replaced with new nodes that have encrypted root volumes. This may cause temporary downtime for workloads operating on the cluster. Ensure you have planned for this downtime before proceeding.
-
Wait for the repave to complete before validating the changes.
Validate
-
Log in to the Amazon EKS console.
-
Find and click on your EKS cluster.
-
Click on the Compute tab and click on one of your worker pools within the Node Groups section.
-
In the Node group configuration section, click Launch template to view the details of the launch template used by the worker pool.
-
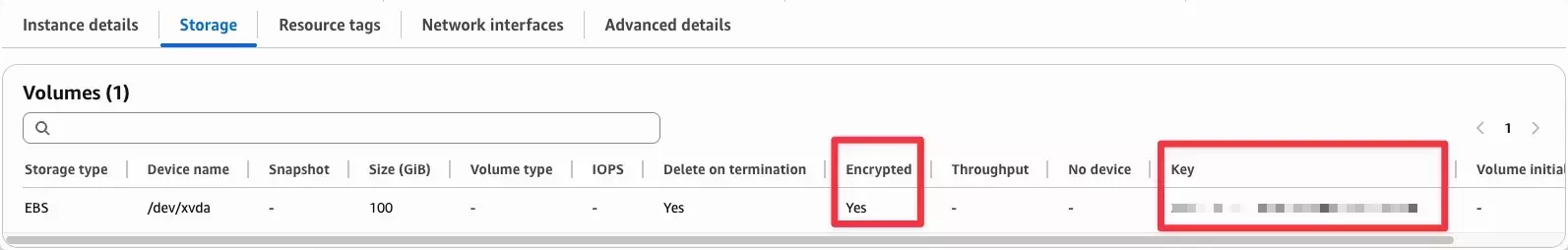
In the Launch template version details section, select the Storage tab.
-
Verify that the volumes are encrypted and that the Key is set to the KMS key ID you specified in the cluster profile.